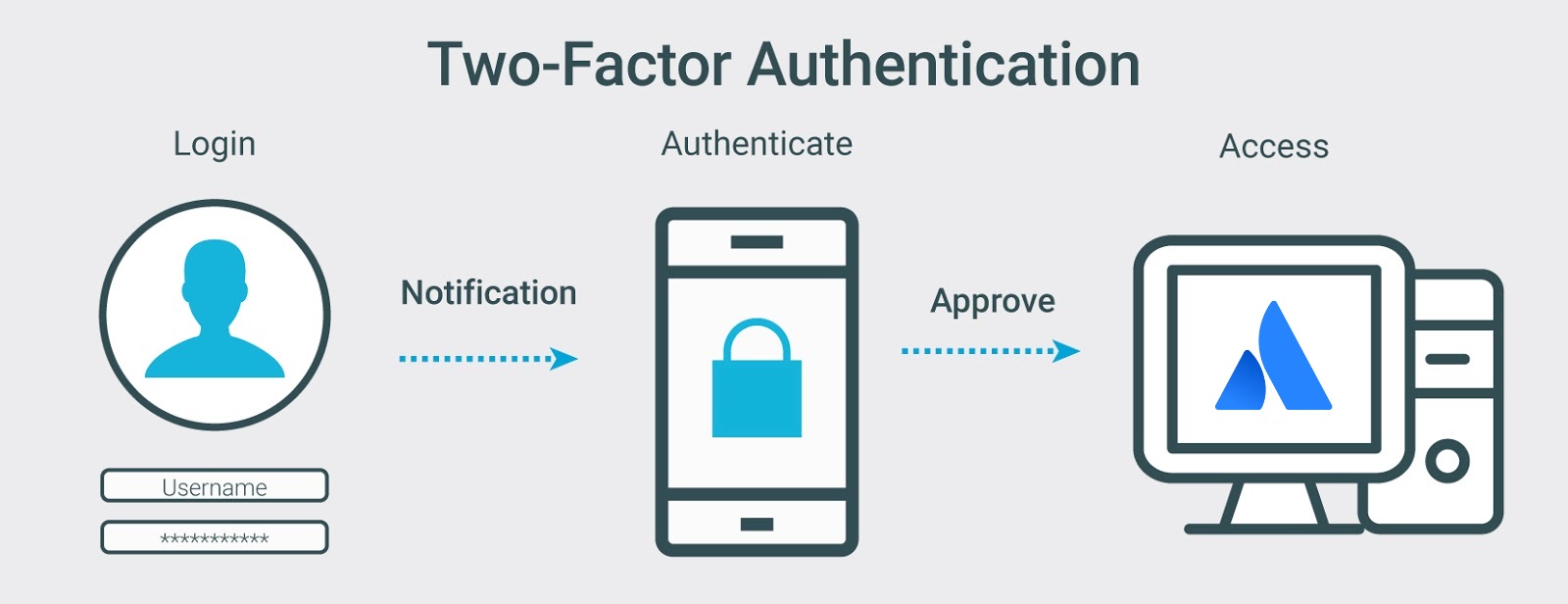
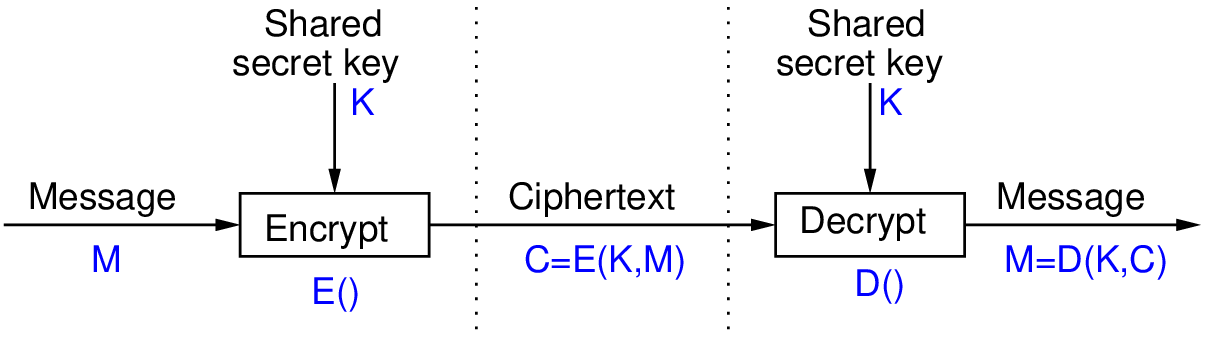
User authentication-authorization concept icon. Software development kit idea thin line illustration. Data encryption. Privacy protection. Application Stock Vector Image & Art - Alamy

The Hidden Costs of DIY Cloud Data Lakes #2: Identity Management and Authentication (Single Sign-On) - Cazena | Cazena
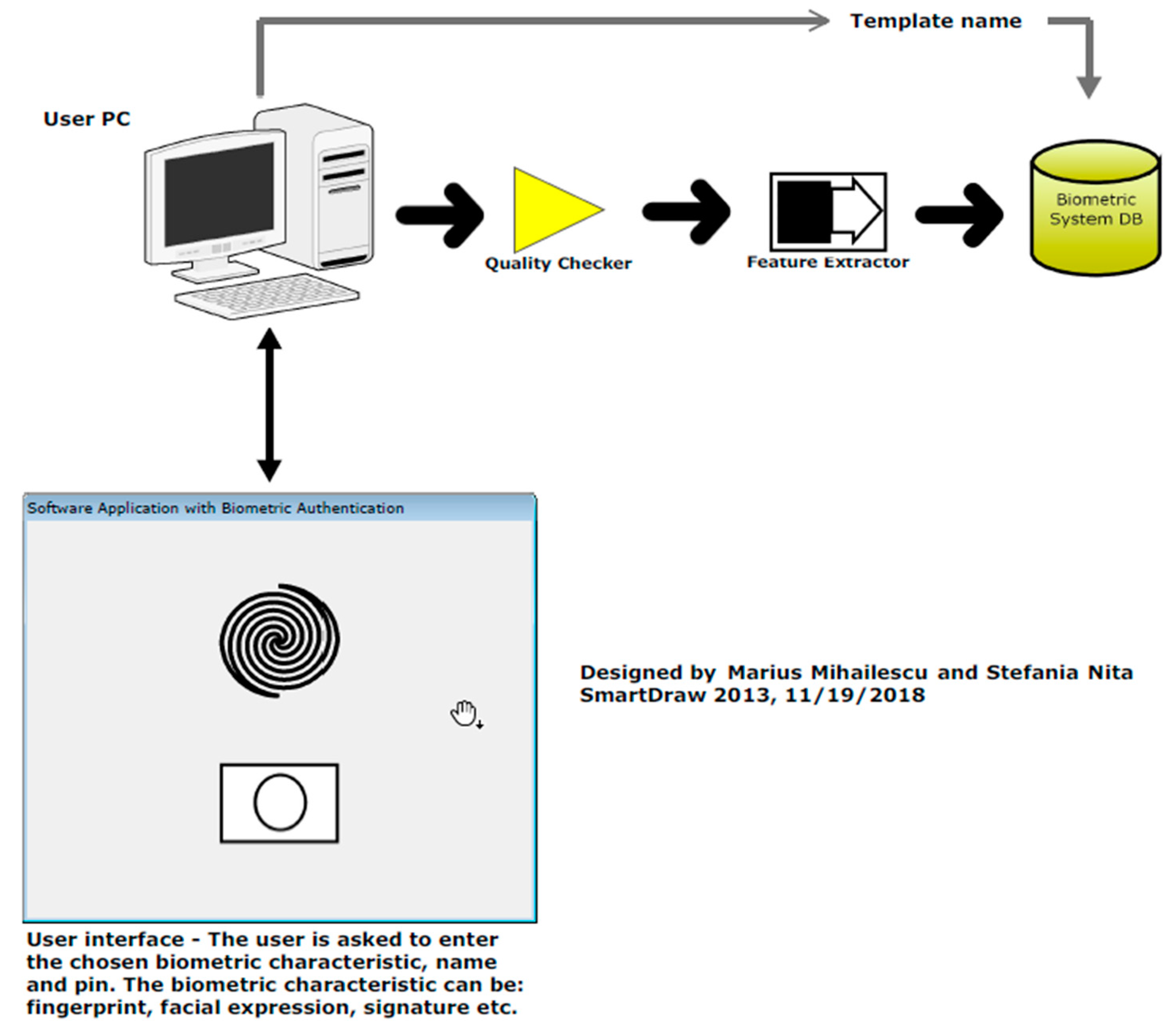
Cryptography | Free Full-Text | Security and Cryptographic Challenges for Authentication Based on Biometrics Data